In the modern world, we rely on technology more and more to make our lives easier. But as this reliance increases, so does the potential for security risks posed by unsecured Internet of Things (IoT) devices connected to a network. That’s why it is essential for organizations and individuals alike to know how to detect IoT devices on networks to keep their data secure from malicious actors.
In this blog post, we’ll explore what an IoT device is, why detecting them on your network is important, how you can do that detection yourself or with help from experts and best practices for securing against any unsecured ones found. So let’s learn together how to detect IoT devices on networks.
Table of Contents
What Are IoT Devices?
IoT devices, or Internet of Things devices, are physical objects that are connected to the internet and can send and receive data. These devices range from simple sensors to complex systems such as self-driving cars. They have become increasingly popular in recent years due to their ability to automate processes and provide valuable insights into our lives.
Definition of IoT Devices
IoT devices are any device with an embedded computer system that is connected to the internet and capable of sending and receiving data. This includes both hardware components (such as microcontrollers) and software components (such as operating systems).
Types of IoT Devices
There are many different types of IoT devices, ranging from simple sensors that measure temperature or humidity levels, to more complex systems such as smart home hubs or autonomous vehicles.
Some common examples include wearables like fitness trackers, security cameras, thermostats, lighting control systems, medical equipment monitors, industrial automation controllers, and agricultural monitoring tools, among others.
IoT devices are becoming increasingly common in our daily lives, and it is important to understand the potential security risks posed by unsecured IoT devices on a network. To protect ourselves from these risks, we must be able to detect and secure any connected IoT devices on a network.
Why Is It Important to Detect IoT Devices on a Network?
The network security risks posed by unsecured IoT devices are a major concern for businesses and individuals alike. Unsecured IoT devices can be used to access sensitive data, launch attacks on other networks, or even gain control of the device itself.
For example, an attacker could use an unsecured IP camera to spy on its surroundings or take control of it remotely. Additionally, these devices often have weak passwords that can easily be guessed or brute-forced by attackers.
Detecting and securing IoT devices is essential to protect your network from malicious actors. By detecting connected IoT devices on your network you can identify any potential vulnerabilities before they become a problem.
This allows you to take steps such as implementing firewall rules and access control lists (ACLs) to prevent unauthorized access and ensure that only authorized users have access to the system’s resources. Additionally, strong passwords should be enforced across all connected devices to further reduce the risk of attack from outside sources.
It is important to detect IoT devices on a network to identify and mitigate any security risks posed by unsecured devices. By understanding how to detect IoT devices on networks, organizations can ensure their networks are secure and benefit from the advantages of using connected technologies.
How to Detect IoT Devices on Networks
Because of the potential security risk involved with unsecured IoT devices, it is important to learn how to detect IoT devices on networks you own. Here are some of the methods for detecting IoT devices.
Scanning the Network for Connected Devices
One of the most effective ways to identify IoT devices on a network is by scanning them for connected devices. This can be done using a variety of tools, such as port scanners, wireless scanners, and packet sniffers.
These tools will help you with device identification and looking at all active connections on your network, including any unknown or suspicious ones that could potentially be from an IoT device.
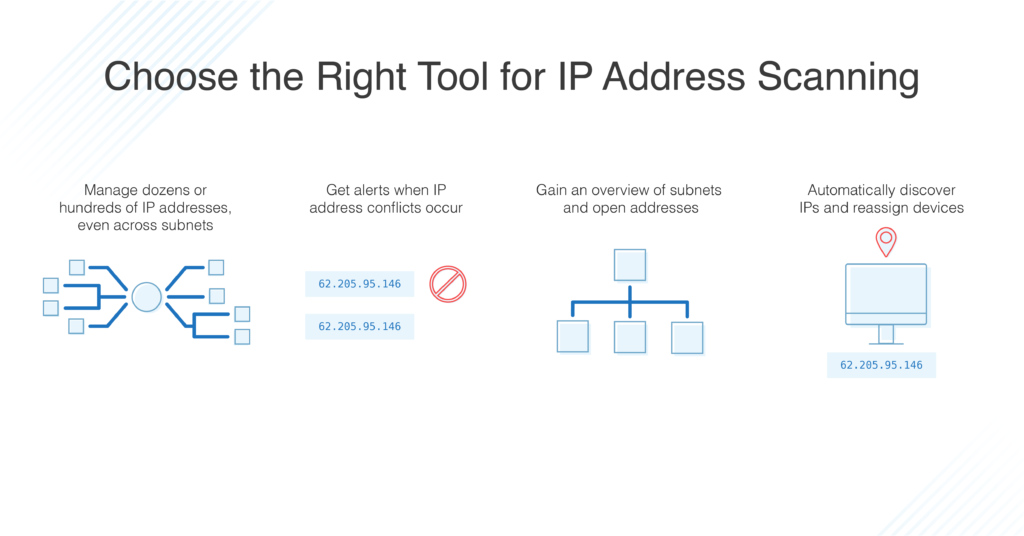
(Source)
Using Network Monitoring Tools to Identify Unknown Connections
Another way to detect IoT devices on a network is by using network monitoring tools such as NetFlow or SNMP (Simple Network Management Protocol). These tools provide detailed information about all traffic going in and out of your network, allowing you to quickly do device identification and pinpoint potential threats.
Device Fingerprinting
Finally, one of the best ways for device identification on a network is through device fingerprinting techniques like MAC address spoofing or IP geolocation tracking. By analyzing various characteristics associated with each connection such as IP addresses, MAC addresses, and DNS records, you can accurately determine which type of device is connecting to your network and take appropriate action if necessary.
By knowing how to detect IoT devices on networks you own, you gain increased security for your business and protect your network from security threats.
Best Practices for Securing Your Network Against Unsecured IoT Devices
Network security against unsecured IoT devices is essential for keeping your data and systems safe.
Implementing firewall rules and access control lists (ACLs) can help protect against malicious traffic. Enforcing strong passwords and multi-factor authentication (MFA) can prevent unauthorized access to sensitive information. Additionally, updating firmware regularly and installing security patches can help ensure that any vulnerabilities in the system are addressed quickly.
Implementing Firewall Rules and Access Control Lists (ACLs)
Firewalls provide an additional layer of protection by blocking unwanted or suspicious traffic from entering a network. ACLs allow administrators to create specific rules about which types of traffic are allowed on the network, helping to keep out malicious actors who may be trying to gain access through vulnerable IoT devices.
Ensure Strong Passwords
Ensuring the use of strong passwords for all users is essential to prevent any unauthorized access to confidential information stored on vulnerable devices. Multi-Factor Authentication (MFA) should be employed whenever possible as it provides an additional layer of security, necessitating that users enter both their username/password combination and a code sent via text message or email before they can log in successfully.
Keep Firmware Updated
It is essential to keep firmware up-to-date to ensure that any known vulnerabilities in the system are patched quickly, preventing them from becoming exploitable entry points for attackers looking to gain access to networks through unsecured IoT devices.
Additionally, security patches released by device manufacturers must be installed promptly after being made available. This is to address any new threats posed by newly discovered exploits before they cause significant damage or disruption.
Securing your network against unsecured and vulnerable devices is essential to protect your data and maintain the security of your system. Several best practices can help you keep your network safe from malicious actors.
Conclusion
It is important to learn how to detect IoT devices on networks you own to ensure the security of your network and data. By understanding what IoT devices are, why they need to be detected, and how to detect them, you can take steps toward protecting your organization from potential threats posed by unsecured IoT devices.
Additionally, following best practices for securing your network against unsecured IoT devices will help protect you from any malicious activity that could occur due to undetected or vulnerable IoT devices on your network. With the right measures in place, you can rest assured that all of the connected device traffic on your network is secure when you detect IoT devices on a network.